Peace of mind, all the time
The software development life cycle is continuous. Traditional cybersecurity tools are not. We help you integrate security monitoring into your SDLC.
We secure some of your favorite applications
Know the risk, make the fix, anytime.
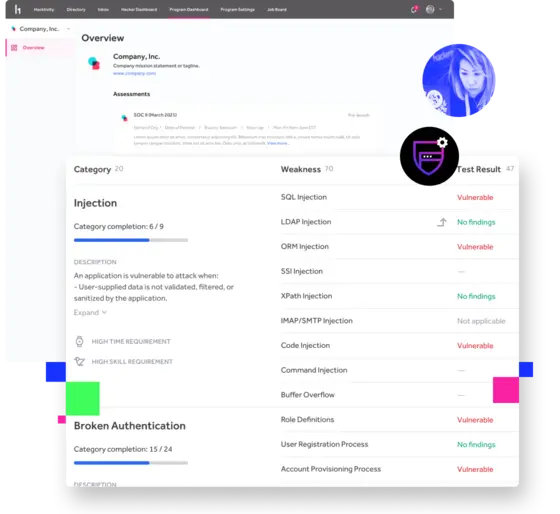
Unified analytics show you the vulnerabilities that pose the greatest threat, and plot your path to remediation.
- Improve and scale software delivery with continuous security testing.
- Engage security experts to help agile teams identify and fix vulnerabilities before they become breaches.
- Launch new applications with confidence, knowing talented hackers have vetted your code.
Compliance checks that won’t slow your pipeline.
As attack surfaces expand, organizations need to rapidly validate their risk profile to assure business continuity, comply with mandates and deliver trusted experiences to customers.
- Quickly meet compliance and regulatory standards to assure your product launches stay on track.
- Measure threats, examine the landscape, and demonstrate value to stakeholders, customers, and partners.
Ready to transform your application security?
Tell us about your application security concerns, and one of our experts will contact you soon.
Next-Gen Application Security
Agile development calls for agile security. Improve your application security by incorporating continuous vulnerability detection and risk assessment—powered by ethical hackers—into your development pipeline.
What Years of AWS Hacking Tells Us About Building Secure Apps
Years of AWS bug bounties have exposed SSRF vulnerabilities, misconfigurations...
How Bug Bounties Help You Shift Left
The Rise of IDOR
Insecure Direct Object References (or IDOR) is a simple bug that packs a punch...













