Power up your Pentesting
Achieve regulatory compliance and satisfy vendor security assessments across web and mobile applications, APIs, and external network infrastructure.
What is Pentest as a Service (PTaaS)?
Pentest as a Service, or PTaaS, is a SaaS delivery model for managing and orchestrating pentesting engagements Penetration testing, or pentesting, is an authorized simulated cyberattack on an organization’s attack surface, performed by human testers to find and assess the severity of vulnerabilities. Pentesting is time bound, typically two weeks in duration, and methodology-driven, with a detailed report of findings delivered post engagement.
How does Pentest as a Service work?
PTaaS solutions provide a means for human pentesters to submit findings in real-time and for customers to consume results, interact with testers, and manage pentest programs on an annual basis. PTaaS, in some cases, also provides access to a community of vetted, background checked ethical hackers for a larger pool of testers with the potential for more diverse perspectives, skills and tactics.
Support your compliance requirements with a diverse testing portfolio
Uncover vulnerable software, weak credentials, and infrastructure misconfigurations across web, mobile, network, API, and desktop assets.
-
Root out vulnerabilities in web and mobile applications to keep your data safe.
-
Find weaknesses in infrastructure that hosts public applications and filters malicious traffic.
-
Test against OWASP top 10 categories and adhere to industry standards.
Get an expert-written summary for auditors and executives
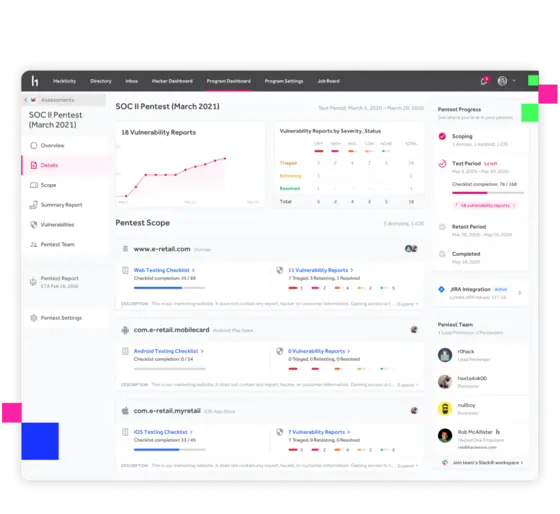
You’ll be able to fix bugs quickly thanks to real-time vulnerability alerts. And at the end of the pentest period you’ll receive a final report that includes key recommendations, the assessed scope, tester profiles, vulnerability details, remediation results, and more.
- Access your report from the HackerOne platform anytime after testing wraps up.
- Download a detailed summary report or a high-level attestation— each customized for your needs and audience.
- Compare AWS Security Hub findings with reports in HackerOne to see duplicates and understand status.
Ready to rethink your traditional pentest?
Tell us about your product, audit, or vendor security assessment needs and one of our experts will contact you.











