Security assessments that check more than boxes
Reduce risk with cyber security assessments of vulnerabilities for cloud configurations, application security, new product launches, and compliance requirements.
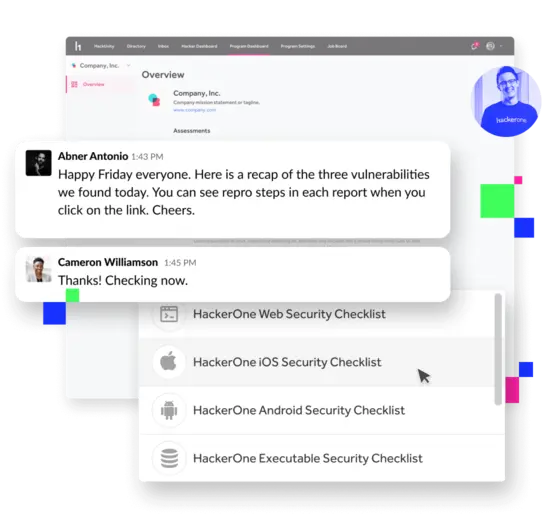
Act on vulnerabilities as they’re reported.
Our platform allows IT and development teams to pinpoint, track, and remediate software vulnerabilities as they’re reported.
- Get notified when vulnerabilities are submitted—no waiting for a final report.
- Receive reports via the HackerOne platform, and communicate with testers to discuss reproducible steps.
- Collaborate directly with testers throughout the engagement.
Make remediation a part of your workflow.
Make security an invisible part of your development process by Integrating vulnerability remediation into existing workflows—never adding needless steps to the software life cycle.
- Send vulnerabilities directly to your workflow via GitHub, Jira, and more.
- Remediate vulnerabilities as they’re found, and verify fixes with the original test team.
- Share an executive summary report with stakeholders, detailing findings, recommendations, and remediation status.
Simplify how you share pentest and assessment results.
Centralize vulnerability findings across various teams running security assessments. Access, track, and share results with peers from a single dashboard.
- See what’s being tested and prioritize your assets through pre-built checklists aligned to OWASP categories.
- Download summary report write-ups with details on CVSS severity and CWE weaknesses.
Level up coverage assurance across your attack surface.
Uncover vulnerable software, weak credentials, and infrastructure misconfigurations across web, mobile, network, API, and desktop assets.
- Test against applications to identify vulnerabilities and adhere to OWASP Top 10 categories like cross-site scripting, broken access controls, and injections.
- Run DNS checks and port scans across your network environment and other security appliances that filter malicious traffic from the internet.
- Identify common mobile security issues: insecure authentication, data storage, communication, and more.
See how it works.
Looking for a vendor to help with security assessments?
Get in contact
What to Look For in a Penetration Testing Company
Penetration testing is one of the most widely used techniques to comply with...